Automate the collection, analysis, and remediation of security vulnerabilities and out-of-compliance conditions

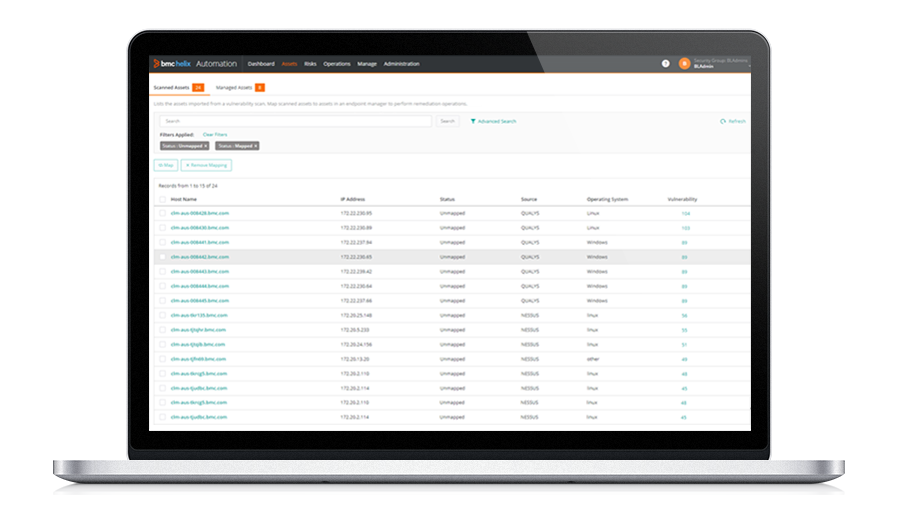
- Automatically import, consolidate, and analyze security vulnerability scanner data
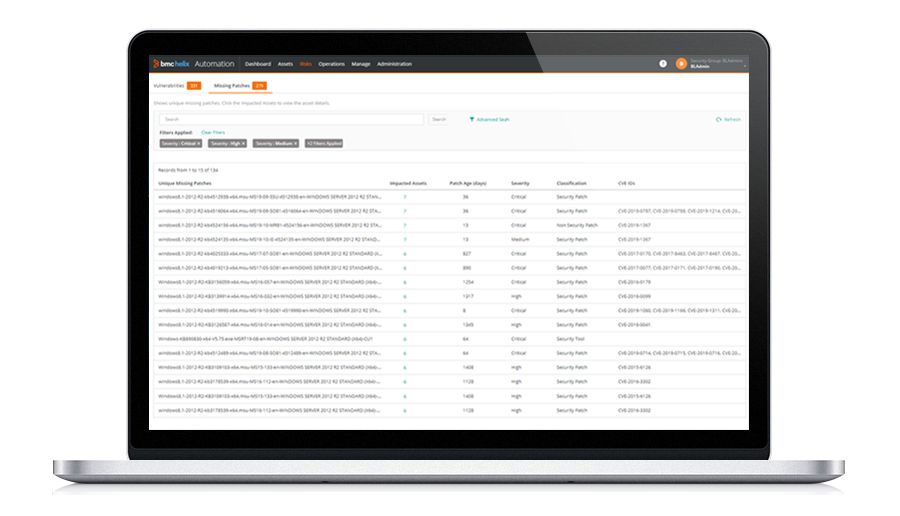
- Take automated corrective action based on vulnerability risk scoring, priorities, and business services exposed to protect data and maintain uptime
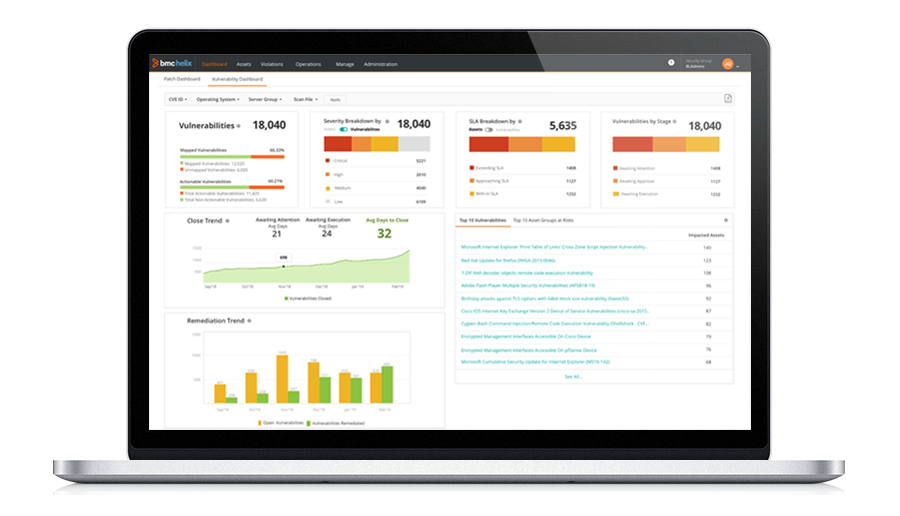
- Leverage drill-down capability for near real-time visibility into patch and vulnerability status, with actionable dashboards for data filtering and executing remediation tasks
- Vulnerability noise reduction prevents viewing vulnerabilities that have already been closed
- Vulnerability exception management and customized tagging improves ease of use and efficiency
- Blind spot detection and closed-loop change and configuration management
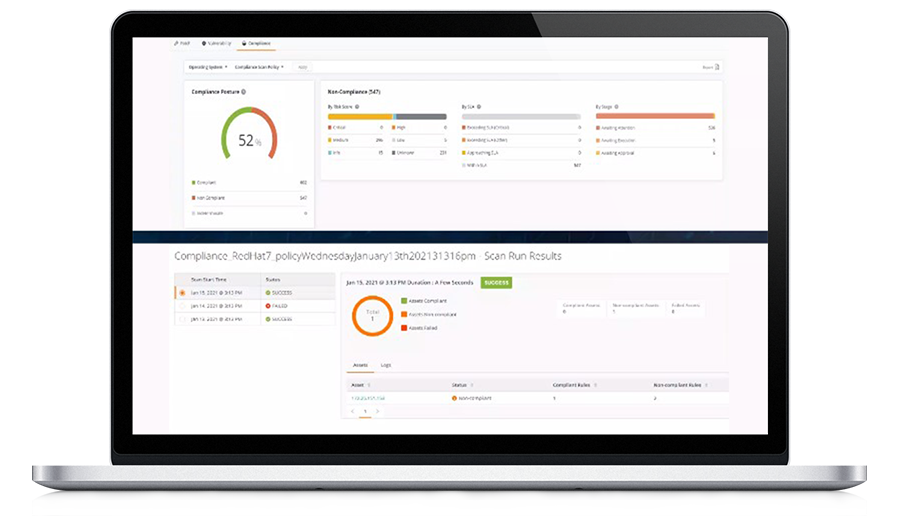
- Automate compliance with regulations (SOX, HIPAA, PCI, CISA, DISA) and internal policies to prevent audit failures and out-of-compliance conditions